Custom Resource Definitions (CRDs) Monitoring¶
Overview¶
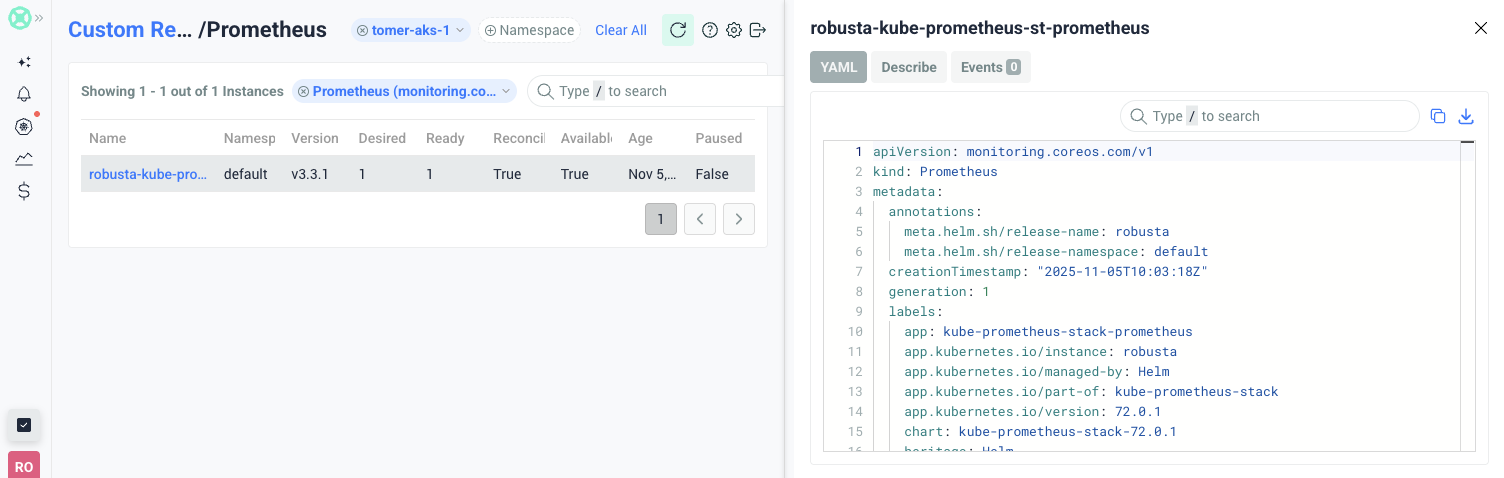
The CRDs monitoring feature enables you to view and manage Custom Resource Definitions and their instances directly from the Robusta UI. This powerful feature provides visibility into:
All CRDs deployed in your clusters
Individual CR (Custom Resource) instances and their status
Resource events and history
Full YAML manifests
Detailed resource descriptions
Prerequisites¶
To enable CRD monitoring, the Robusta agent needs appropriate permissions to read custom resources in your cluster. This requires adding cluster role rules to your Robusta configuration.
Configuration¶
Finding CRD Names and API Groups¶
Get the CRD names and API groups to use in the configuration below:
kubectl get crd \
-o custom-columns=NAME:.spec.names.plural,API_GROUP:.spec.group
This will output something like:
NAME API_GROUP
alertmanagerconfigs monitoring.coreos.com
alertmanagers monitoring.coreos.com
imagejobs eraser.sh
imagelists eraser.sh
nodenetworkconfigs acn.azure.com
overlayextensionconfigs acn.azure.com
...
Basic Configuration¶
Specify read permissions for the CRDs you need to monitor. You can list specific resources or use "*" to monitor all resources in an API group:
runner:
customClusterRoleRules:
- apiGroups:
- "cert-manager.io"
resources:
- "certificates"
- "certificaterequests"
- "issuers"
- "clusterissuers"
verbs:
- "list"
- "get"
Or to monitor all resources in an API group:
runner:
customClusterRoleRules:
- apiGroups:
- "cert-manager.io"
resources:
- "*"
verbs:
- "list"
- "get"
Default CRD Permissions¶
Robusta includes read-only permissions for common Kubernetes operators and tools by default. These can be individually enabled or disabled:
runner:
crdPermissions:
argo: true # Argo CD, Argo Workflows, Argo Rollouts
flux: true # Flux CD (GitOps toolkit)
kafka: true # Strimzi Kafka
keda: true # KEDA autoscaler
crossplane: true # Crossplane
istio: true # Istio service mesh
gatewayApi: true # Kubernetes Gateway API
velero: true # Velero backup/restore
externalSecrets: true # External Secrets Operator
Applying the Configuration¶
Update your
values.yamlfile with the desired configurationApply the changes using Helm:
helm upgrade robusta robusta/robusta \
--values values.yaml \
--namespace robusta \
--reuse-values
Automatic Configuration with Holmes AI¶
Instead of manually configuring permissions for each CRD, you can use Holmes AI to automatically generate the configuration for all CRDs in your cluster.
Using Holmes to Generate Configuration¶
Navigate to the Holmes Ask page in the Robusta UI
Use the following prompt:
I want to add read only cluster roles for all the crds in my cluster.
This is the format for adding one:
runner:
customClusterRoleRules:
- apiGroups:
- "storage.k8s.io"
resources:
- "storageclasses"
verbs:
- "list"
- "get"
Prepare my config
Holmes will analyze your cluster and generate a complete configuration including all CRDs
Copy the generated configuration and add it to your
values.yamlApply the configuration using Helm as described above
Tip
After Holmes generates the configuration, you can review and modify it to remove any CRDs you don't want to monitor before applying it.
Troubleshooting¶
Common Issues and Solutions¶
Issue 1: CRDs not appearing in UI
Check permissions: Verify the ClusterRole has the correct permissions
kubectl get clusterrole robusta-runner -o yamlCheck agent logs: Look for permission errors
kubectl logs -n robusta deployment/robusta-runner | grep -i "forbidden"
Issue 2: "Forbidden" errors when accessing CRDs
Solution: Add the specific apiGroup and resource to
customClusterRoleRulesExample error:
cannot get resource "certificates" in API group "cert-manager.io"Fix: Add the cert-manager.io apiGroup with certificates resource